ni:///sha-1;aGxsejhHVGRzbmJsRDd0LzBJbHFCN0Y3aTdjPQ?http=ods-qa.openlinksw.com
Conditional Sharing – Virtuoso ACL Groups Revisited
Previously we saw how ACLs can be used in Virtuoso to protect different types of resources. Today we will look into conditional groups which allow to share resources or grant permissions to a dynamic group of individuals. This means that we do not maintain a list of group members but instead define a set of conditions which an individual needs to fulfill in order to be part of the group in question.
That does sound very dry. Let’s just jump to an example:
@prefix oplacl: <http://www.openlinksw.com/ontology/acl#> .
[] a oplacl:ConditionalGroup ;
foaf:name "People I know" ;
oplacl:hasCondition [
a oplacl:QueryCondition ;
oplacl:hasQuery """ask where { graph <urn:my> { <urn:me> foaf:knows ^{uri}^ } }"""
] .
This group is based on a single condition which uses a simple SPARQL ASK query. The ask query contains a variable ^{uri}^ which the ACL engine will replace with the URI of the authenticated user. The group contains anyone who is in a foaf:knows relationship to urn:me in named graph urn:my. (Ideally the latter graph should be write-protected using ACLs as described before.)
Now we use this group in ACL rules. That means we first create it:
$ curl -X POST \
--data-binary @group.ttl \
-H"Content-Type: text/turtle" \
-u dba:dba \
http://localhost:8890/acl/groups
As a result we get a description of the newly created group which also contains its URI. Let’s imagine this URI is http://localhost:8890/acl/groups/1.
To mix things up we will use the group for sharing permission to access a service instead of files or named graphs. Like many of the Virtuoso-hosted services the URI Shortener is ACL controlled. We can restrict access to it using ACLs.
As always the URI Shortener has its own ACL scope which we need to enable for the ACL system to kick in:
sparql
prefix oplacl: <http://www.openlinksw.com/ontology/acl#>
with <urn:virtuoso:val:config>
delete {
oplacl:DefaultRealm oplacl:hasDisabledAclScope <urn:virtuoso:val:scopes:curi> .
}
insert {
oplacl:DefaultRealm oplacl:hasEnabledAclScope <urn:virtuoso:val:scopes:curi> .
};
Now we can go ahead and create our new ACL rule which allows anyone in our conditional group to shorten URLs:
[] a acl:Authorization ; oplacl:hasAccessMode oplacl:Write ; acl:accessTo <http://localhost:8890/c> ; acl:agent <http://localhost:8890/acl/groups/1> ; oplacl:hasScope <urn:virtuoso:val:scopes:curi> ; oplacl:hasRealm oplacl:DefaultRealm .
Finally we add one URI to the conditional group as follows:
sparql
insert into <urn:my> {
<urn:me> foaf:knows <http://www.facebook.com/sebastian.trug> .
};
As a result my facebook account has access to the URL Shortener:

The example we saw here uses a simple query to determine the members of the conditional group. These queries could get much more complex and multiple query conditions could be combined. In addition Virtuoso handles a set of non-query conditions (see also oplacl:GenericCondition). The most basic one being the following which matches any authenticated person:
[] a oplacl:ConditionalGroup ;
foaf:name "Valid Identifiers" ;
oplacl:hasCondition [
a oplacl:GroupCondition, oplacl:GenericCondition ;
oplacl:hasCriteria oplacl:NetID ;
oplacl:hasComparator oplacl:IsNotNull ;
oplacl:hasValue 1
] .
This shall be enough on conditional groups for today. There will be more playing around with ACLs in the future…
Protecting And Sharing Linked Data With Virtuoso
Disclaimer: Many of the features presented here are rather new and can not be found in the open-source version of Virtuoso.
Last time we saw how to share files and folders stored in the Virtuoso DAV system. Today we will protect and share data stored in Virtuoso’s Triple Store – we will share RDF data.
Virtuoso is actually a quadruple-store which means each triple lives in a named graph. In Virtuoso named graphs can be public or private (in reality it is a bit more complex than that but this view on things is sufficient for our purposes), public graphs being readable and writable by anyone who has permission to read or write in general, private graphs only being readable and writable by administrators and those to which named graph permissions have been granted. The latter case is what interests us today.
We will start by inserting some triples into a named graph as dba – the master of the Virtuoso universe:
This graph is now public and can be queried by anyone. Since we want to make it private we quickly need to change into a SQL session since this part is typically performed by an application rather than manually:
$ isql-v localhost:1112 dba dba
Connected to OpenLink Virtuoso
Driver: 07.10.3211 OpenLink Virtuoso ODBC Driver
OpenLink Interactive SQL (Virtuoso), version 0.9849b.
Type HELP; for help and EXIT; to exit.
SQL> DB.DBA.RDF_GRAPH_GROUP_INS ('http://www.openlinksw.com/schemas/virtrdf#PrivateGraphs', 'urn:trueg:demo');
Done. -- 2 msec.
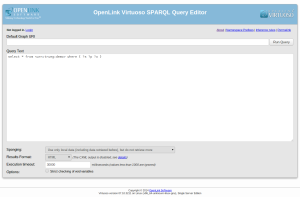
Now our new named graph urn:trueg:demo is private and its contents cannot be seen by anyone. We can easily test this by logging out and trying to query the graph:
But now we want to share the contents of this named graph with someone. Like before we will use my LinkedIn account. This time, however, we will not use a UI but Virtuoso’s RESTful ACL API to create the necessary rules for sharing the named graph. The API uses Turtle as its main input format. Thus, we will describe the ACL rule used to share the contents of the named graph as follows.
@prefix acl: <http://www.w3.org/ns/auth/acl#> . @prefix oplacl: <http://www.openlinksw.com/ontology/acl#> . <#rule> a acl:Authorization ; rdfs:label "Share Demo Graph with trueg's LinkedIn account" ; acl:agent <http://www.linkedin.com/in/trueg> ; acl:accessTo <urn:trueg:demo> ; oplacl:hasAccessMode oplacl:Read ; oplacl:hasScope oplacl:PrivateGraphs .
Virtuoso makes use of the ACL ontology proposed by the W3C and extends on it with several custom classes and properties in the OpenLink ACL Ontology. Most of this little Turtle snippet should be obvious: we create an Authorization resource which grants Read access to urn:trueg:demo for agent http://www.linkedin.com/in/trueg. The only tricky part is the scope. Virtuoso has the concept of ACL scopes which group rules by their resource type. In this case the scope is private graphs, another typical scope would be DAV resources.
Given that file rule.ttl contains the above resource we can post the rule via the RESTful ACL API:
$ curl -X POST --data-binary @rule.ttl -H"Content-Type: text/turtle" -u dba:dba http://localhost:8890/acl/rules
As a result we get the full rule resource including additional properties added by the API.
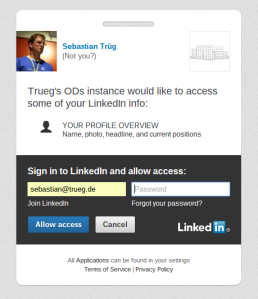
Finally we will login using my LinkedIn identity and are granted read access to the graph:
We see all the original triples in the private graph. And as before with DAV resources no local account is necessary to get access to named graphs. Of course we can also grant write access, use groups, etc.. But those are topics for another day.
Technical Footnote
Using ACLs with named graphs as described in this article requires some basic configuration. The ACL system is disabled by default. In order to enable it for the default application realm (another topic for another day) the following SPARQL statement needs to be executed as administrator:
sparql
prefix oplacl: <http://www.openlinksw.com/ontology/acl#>
with <urn:virtuoso:val:config>
delete {
oplacl:DefaultRealm oplacl:hasDisabledAclScope oplacl:Query , oplacl:PrivateGraphs .
}
insert {
oplacl:DefaultRealm oplacl:hasEnabledAclScope oplacl:Query , oplacl:PrivateGraphs .
};
This will enable ACLs for named graphs and SPARQL in general. Finally the LinkedIn account from the example requires generic SPARQL read permissions. The simplest approach is to just allow anyone to SPARQL read:
@prefix acl: <http://www.w3.org/ns/auth/acl#> . @prefix oplacl: <http://www.openlinksw.com/ontology/acl#> . <#rule> a acl:Authorization ; rdfs:label "Allow Anyone to SPARQL Read" ; acl:agentClass foaf:Agent ; acl:accessTo <urn:virtuoso:access:sparql> ; oplacl:hasAccessMode oplacl:Read ; oplacl:hasScope oplacl:Query .
I will explain these technical concepts in more detail in another article.
Sharing Files With Whomever Is Simple
Dropbox, Google Drive, OneDrive, Box.com – they all allow you to share files with others. But they all do it via the strange concept of public links. Anyone who has this link has access to the file. On first glance this might be easy enough but what if you want to revoke read access for just one of those people? What if you want to share a set of files with a whole group?
I will not answer these questions per se. I will show an alternative based on OpenLink Virtuoso.
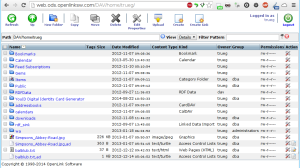
Virtuoso has its own WebDAV file storage system built in. Thus, any instance of Virtuoso can store files and serve these files via the WebDAV API (and an LDP API for those interested) and an HTML UI. See below for a basic example:
This is just your typical file browser listing – nothing fancy. The fancy part lives under the hood in what we call VAL – the Virtuoso Authentication and Authorization Layer.
We can edit the permissions of one file or folder and share it with anyone we like. And this is where it gets interesting: instead of sharing with an email address or a user account on the Virtuoso instance we can share with people using their identifiers from any of the supported services. This includes Facebook, Twitter, LinkedIn, WordPress, Yahoo, Mozilla Persona, and the list goes on.
For this small demo I will share a file with my LinkedIn identity http://www.linkedin.com/in/trueg. (Virtuoso/VAL identifier people via URIs, thus, it has schemes for all supported services. For a complete list see the Service ID Examples in the ODS API documentation.)
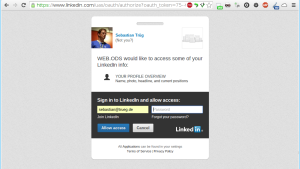
Now when I logout and try to access the file in question I am presented with the authentication dialog from VAL:
This dialog allows me to authenticate using any of the supported authentication methods. In this case I will choose to authenticate via LinkedIn which will result in an OAuth handshake followed by the granted read access to the file:
It is that simple. Of course these identifiers can also be used in groups, allowing to share files and folders with a set of people instead of just one individual.
Next up: Sharing Named Graphs via VAL.
YouID Identity Claim
di:sha1;eCt+TB1Pj/vgY05nqB48sd1seqo=?http=trueg.selfhost.eu%3A8899
TPAC 2012 – Who Am I (On the Web)?
Last week I attended my first TPAC ever – in Lyon, France. Coming from the open-source world and such events like Fosdem or the ever brilliant Akademy I was not sure what to expect. Should I pack a suite? On arrival all my fears were blown away by an incredibly well organized event with a lot of nice people. I felt very welcome as a newbie, there was even a breakfast for the first-timers with some short presentations to get an overview of the W3C‘s work in general and the existing working groups. So before getting into any details: I would love this to become a regular thing (not sure it will though, seeing that next year the TPAC will be in China).

My main reason for going to the TPAC was identity on the Web, or short WebID. OpenLink Software is a strong supporter of the WebID identification and authentication system. Thus, it was important to be present for the meeting of the WebID community group.
The meeting with roughly 15 people spawned some interesting discussions. The most heatedly debated topic was that of splitting the WebID protocol into two parts: 1. identification and 2. authentication. The reason for this is not at all technical but more political. The WebID protocol which uses public keys embedded in RDF profiles and X.509 certificates which contain a personal profile URL has always had trouble being accepted by several working groups and people. So in order to lower the barrier for acceptance and to level the playing field the idea was to split the part which is indisputable (at least in the semantic web world) from the part that people really have a problem with (TLS).
This lead to a very simple definition of a WebID which I will repeat in my own words since it is not written in stone yet (or rather “written in spec”):
A WebID is a dereferencable URI which denotes an agent (person, organization, or software). It resolves to an RDF profile document uniquely identifying the agent.
Here “uniquely identify” simply means that the profile contains some relation of the WebID to another identifier. This identifier can be an email address (foaf:mbox), it can be a Twitter account, an OpenID, or, to restore the connection to the WebID protocol, a public key.
The nice thing about this separation of identity and authentication is that the WebID is now compatible with any of the authentication systems out there. It can be used with WebID-Auth (this is how I call the X.509 certificate + public key in agent profile system formally known as WebID), but also with OpenID or even with OAuth. Imagine a service provider like Google returning a WebID as part of the OAuth authentication result. In case of an OpenID the OpenID itself could be the WebID or another WebID would be returned after successful authentication. Then the client could dereference it to get additional information.
This is especially interesting when it comes to WebACLs. Now we could imagine defining WebACLs on WebIDs from any source. Using mutual owl:sameAs relations these WebIDs could be made to denote the same person which the authorizing service could then use to build a list of identifiers that map the one used in the ACL rule.
In any case this is a definition that should pose no problems to such working groups as the Linked Data Protocol. Even the OpenID or OAuth community should wee the benefits of identifying people via URIs. In the end the Web is a Web of URIs…
And Now For Something Completely Different: Resizable Bootstrap Modals
(Update: Now with better overflow handling.)
I have been doing more CSS + JS as I would have liked these past months. I am still a newbie but today I did something which I am happy enough about to make it into a short blog post.
Twitter’s Bootstrap CSS framework is a nice basis to get your web page going. It also has modal windows. JQuery has the resizable function which allows to add resize handles to any div. In order to make this work with a Bootstrap modal I did the following things:
1. Slightly change the positioning of the jQuery resize handles so they do not force scrollbars on the Bootstrap modal and do not add a weird border:
.ui-resizable-s {
bottom: 0;
}
.ui-resizable-e {
right: 0;
}
2. A little bit of JS magic to properly reposition the modal once it has been resized:
$(".modal").on("resize", function(event, ui) {
ui.element.css("margin-left", -ui.size.width/2);
ui.element.css("margin-top", -ui.size.height/2);
ui.element.css("top", "50%");
ui.element.css("left", "50%");
$(ui.element).find(".modal-body").each(function() {
$(this).css("max-height", 400 + ui.size.height - ui.originalSize.height);
});
});
Just look at the Bootstrap modal’s margin in Firebug or something similar to understand the first two statements. The top and left values are to fix the positioning in Opera. The last statement is to also resize the modal body for proper overflow handling.
Now just enable resize on all modals or on whatever modal you want:
$(".modal").resizable();
Digitally Sign Emails With Your X.509 Certificate in Evolution
Digitally signing Emails is always a good idea. People can verify that you actually sent the mail and they can encrypt emails in return. A while ago Kingsley showed how to sign emails in Thunderbird.I will now follow up with a short post on how to do the same in Evolution.
The process begins with actually getting an X.509 certificate including an embedded WebID. There are a few services out there that can help with this, most notably OpenLink’s own YouID and ODS. The former allows you to create a new certificate based on existing social service accounts. The latter requires you to create an ODS account and then create a new certificate via Profile edit -> Security -> Certificate Generator. In any case make sure to use the same email address for the certificate that you will be using for email sending.
The certificate will actually be created by the web browser, making sure that the private key is safe.
If you are a Google Chrome user you can skip the next step since Evolution shares its key storage with Chrome (and several other applications). If you are a user of Firefox you need to perform one extra step: go to the Firefox preferences, into the advanced section, click the “Certificates” button, choose the previously created certificate, and export it to a .p12 file.
Back in Evolution’s settings you can now import this file:
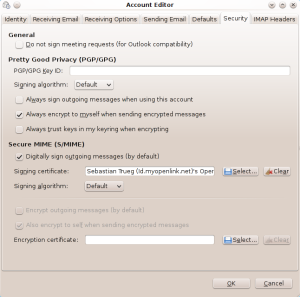
 To actually sign emails with your shiny new certificate stay in the Evolution settings, choose to edit the Mail Account in question, select the certificate in the Secure MIME (S/MIME) section and check “Digitally sign outgoing messages (by default)“:
To actually sign emails with your shiny new certificate stay in the Evolution settings, choose to edit the Mail Account in question, select the certificate in the Secure MIME (S/MIME) section and check “Digitally sign outgoing messages (by default)“:
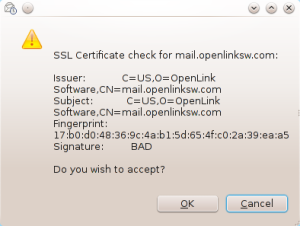
 The nice thing about Evolution here is that in contrast to Thunderbird there is no need to manually import the root certificate which was used to sign your certificate (in our case the one from OpenLink). Evolution will simply ask you to trust that certificate the first time you try to send a signed email:
The nice thing about Evolution here is that in contrast to Thunderbird there is no need to manually import the root certificate which was used to sign your certificate (in our case the one from OpenLink). Evolution will simply ask you to trust that certificate the first time you try to send a signed email:
Use an X.509 certificate for SSH Login
An X.509 certificate contains a private and a public key. As such it is suitable for password-less login via SSH. However, as always with certificates and keys and all that powerful stuff the handling of it all is very clumsy. Kingsley just explained how to setup SSH with X.509 certificates. I will try to add the missing pieces here.
- If you do not have a X.509 certificate yet create one with an embedded WebID via the OpenLink YouID service. Make sure the details actually get saved in the last step, for example by posting an identity claim to your Twitter or LinkedIn accounts. This will make the YouID service persist your profile which in turn will result in your new WebID being dereferencable. Kingsley has some nice Linked data details on that in his post.
- Export the new certificate which should now be installed in your browser’s key store, into a P12 file. This can be done via the certificate viewer in the browser preferences.
- Convert the P12 into PEM format:
# openssl pkcs12 -in MyCert.p12 -out MyCert.pem -nodes
- Extract the private key from the P12:
# openssl pkcs12 -in MyCert.p12 -out MySSHKeys.pem -nodes -nocerts
- Finally extract the public key from the certificate PEM file and append it to the private key:
# openssl x509 -in MyCert.pem -pubkey -noout >> MySSHKeys.pem
- MyCert.pem can now be removed. It is not required anymore.
- You can use ssh-keygen to create the line to put into your remote ~/.ssh/authorized_keysfile:
# ssh-keygen -i -m PKCS8 -f MySSHKeys.pem
Now you are ready to take your shiny new login stuff for a test drive and log into your remote account via:
# ssh -i MySSHKeys.pem user@REMOTE
And to put the cherry on top you can tell ssh to always use that key with the host in question by adding the following block to your client’s ~/.ssh/config file:
Host REMOTE IdentityFile ~/MySSHKeys.pem
This makes login even easier:
# ssh user@REMOTE
Virtuoso 6.1.6 and KDE 4.9
Shortly after KDE 4.9 hits the net Virtuoso 6.1.6 follows. Virtuoso 6.1.6 comes with a ton of fixes, improvements and optimizations and it is highly recommended to update for the best Nepomuk experience.
Virtuoso 6.1.6 has been tested by the Nepomuk team in cooperation with OpenLink Software before its release. It is the recommended release for Nepomuk. This is not only true for KDE 4.9 but for any version before it.
Get the sources while they are hot and build your packages.